
In this article we will learn what the TCP 3-way handshake is, what the most common attacks are and how we can defend ourselves from them, as far as possible.
TCP (Transmission Control Protocol)
First of all, we should know that TCP is the protocol that controls communications between two networked computers.
The TCP protocol is the protocol that allows us to connect to a web server and surf the Internet. It also allows us to connect to our mail server and send or receive emails.
The TCP protocol coordinates the transmission and reception of network packets between two computers so that there is no duplicated, missing or disordered information.
The TCP protocol is connection-oriented, that is, it allows establishing a temporary connection channel between two computers for the mutual sending of information through a network connection.
What the TCP protocol is used for
The TCP protocol is used for all connections that require a round trip communication channel, for example: HTTP, HTTPS, FTP, SSH, SMTP, POP, IMAP, TELNET. This includes, web servers, file servers, mail servers, among others.
How it works
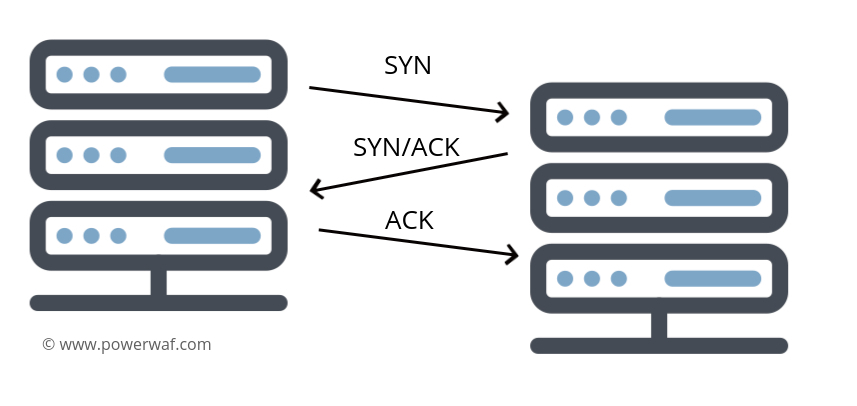
It all starts when one computer needs to connect to another to start an exchange of information. This is where the 3-way handshake is defined.
- Computer 1 sends a packet called SYN to the server and waits for a response.
- The server, when it receives a SYN packet responds with a packet called SYN-ACK and is put on hold.
- Computer 1 receives the SYN-ACK packet, which tells it that the server received the initial packet. It then sends an ACK packet.
- The server receives the ACK packet and data transmission begins.
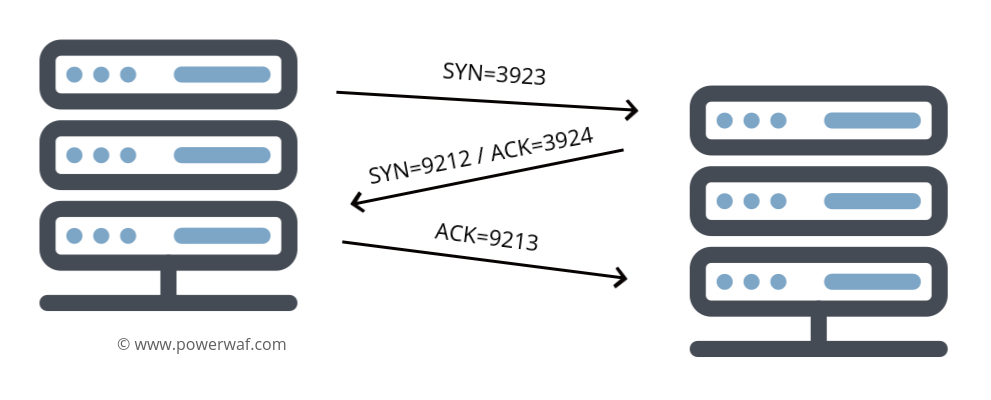
Each packet must have a sequence number, which in its origin is a random number, but the responding server must increase it by one unit. In this way, a real connection looks like this:
Attacks on the TCP protocol
Considering the description above, we can explain one of the most used forms of attack today, of which 8.4 million were reported to have been carried out in 2019. It is the SYNFLOOD attack.
The aim of this type of attack is to provoke the denial of service, i.e. the server that is being attacked is unable to deal correctly with legitimate requests.
This form of attack is described in document RFC-4987
Discovered in 1994 by Bill Cheswick and Steve Bellovin, it is based on the fact that every server that is in a state of listening to new connections, every time it receives a SYN packet, must store in some zone of the memory a data structure waiting to receive the ACK packet. This storage zone is not infinite, but it must have a maximum limit of structures that can be stored.
We have seen surprisingly that many servers have a maximum limit of 128 or 256 structures. Although this configuration can be modified by the administrator, it is incredible to know that it is left at that number.
Then, the attack consists of sending many SYN packets and never responding with an ACK packet, overflowing the server’s memory reserved for it, which produces denial of service and no other server can connect to it.
The intention of a SYN packet flooding attack is not to overload the network nor to wipe out the server’s memory, but simply to fill the table reserved for the unfinished connections on the server, which happens very quickly.
That is why denial of service attacks are a crime in several countries, such as the United States, the European Union, among others, which is punishable by several years in prison.
How do we defend ourselves?
Depending on the complexity of the attack, the defence basically consists of filtering the attacking IP addresses. However, this requires constant monitoring of servers and pending connections. However, we must bear in mind that many times the source IP addresses can be spoofed.
Another approach is to limit the number of new concurrent connections per IP, but, as mentioned above, it is possible for the attacker to send packets with a spoofed source address. We will see this type of attack in a future article.
There are other methods, such as SYN CACHE and SYN COOKIES, which have proven to be very effective in defending against SYN packet flooding attacks. The configuration of these systems requires a correct configuration of the kernel and specific rules for the firewall in the operating system. We will see in another article more details about these techniques.
However, it is necessary to have some kind of defense, since nowadays, it is very easy to carry out an attack of this type, and it is enough to execute it from a single computer to cause the denial of service in any server.
At PowerWAF we work to deliver the best protection against this and other types of attacks.
If you want more information about the attacks on the TCP/IP protocol, like DDoS attacks or Slowloris attack, see our Learning Center with many articles about this topic.