The Slowloris Attack
Slowloris Attack, the Silent Killer of Websites
Imagine a scenario where you are running a popular website that receives thousands of visitors every day. You have invested a lot of time and money to create a fast and reliable web server that can handle the traffic and deliver the content to your users. Everything seems to be working fine until one day, your website suddenly becomes slow and unresponsive. You check your server logs and find out that there is no spike in traffic or any error messages. You try to restart your server but nothing changes. You wonder what is going on and how to fix it.
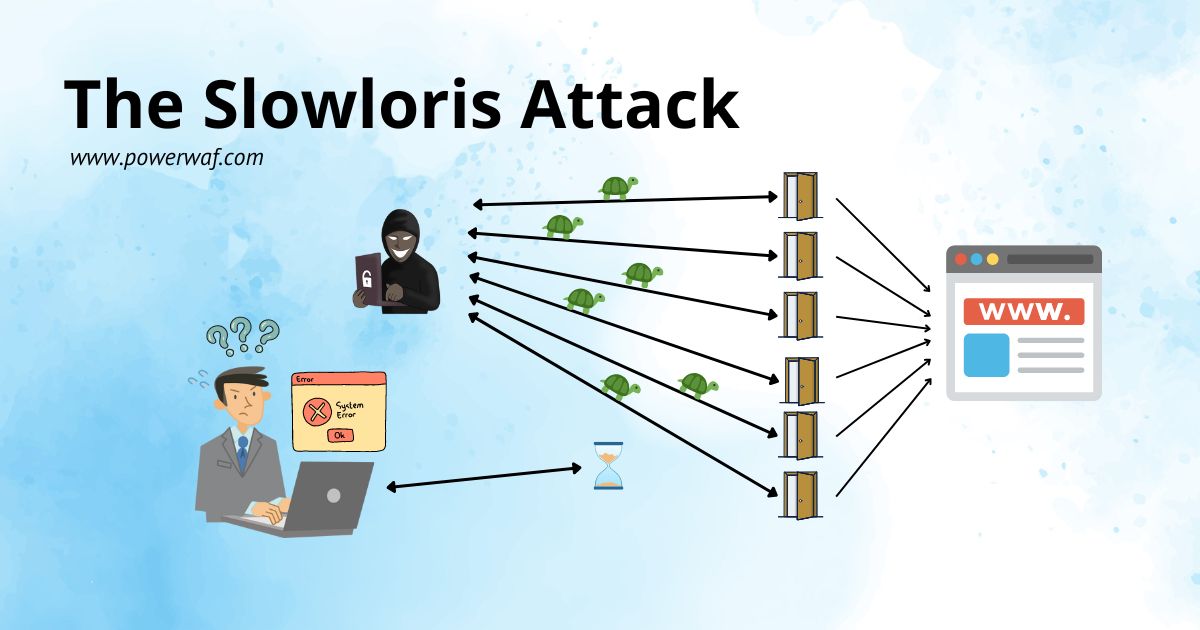
You may be a victim of a Slowloris attack, one of the most stealthy and effective types of denial-of-service (DoS) attacks that can cripple your website without you even noticing it. The Slowloris attack is a technique that exploits a flaw in the way some web servers handle HTTP requests. By sending incomplete or malformed requests to the server, an attacker can keep the server busy and prevent it from processing legitimate requests from other users. Unlike other DoS attacks that rely on flooding the server with a large amount of traffic, a Slowloris attack can be performed with a single machine and a low bandwidth.
In this article, we will explain what a Slowloris attack is and how it works, what impact it can have on your web server and application, how to detect and prevent it, and what best practices you can follow to mitigate it. We will also provide some examples and case studies of Slowloris attacks that have affected real websites in the past. By the end of this article, you will have a better understanding of this silent killer of websites and how to protect yourself from it.
The Definition and History of Slowloris Attacks
The name “Slowloris” may sound cute and harmless, but don’t let it fool you. A Slowloris is actually a type of nocturnal primate that lives in Southeast Asia and Africa. It has a round head, big eyes, and a long tongue that it uses to catch insects and lick venomous glands on its elbows. It moves very slowly and quietly, making it hard to detect by predators and prey alike. It can also mimic a dead branch or a snake to avoid being noticed.
A Slowloris attack is inspired by this animal’s behavior and appearance. It is a DoS attack that mimics a normal HTTP request but never completes it, keeping the server waiting for more data. It moves very slowly and quietly, making it hard to detect by firewalls and intrusion detection systems. It can also mimic a legitimate user or a browser to avoid being blocked.
The first public mention of a Slowloris attack was in 2009, when a security researcher named Robert “RSnake” Hansen published a blog post and a Perl script that demonstrated how to perform the attack. He named the attack after the Slowloris primate because he found it amusing and ironic. He also claimed that he had discovered the attack several years earlier but had kept it secret until then.
Since then, many variants and implementations of the Slowloris attack have emerged, such as PyLoris, SlowHTTPTest, OWASP HTTP Post Tool, and more. Some of them have added features such as encryption, proxy support, randomization, and multithreading. Some of them have also targeted specific web servers or protocols, such as Apache HTTP Server, Internet Information Services (IIS), Secure Sockets Layer (SSL), Hypertext Transfer Protocol Secure (HTTPS), and more.
The Slowloris attack has been used by various actors for different purposes, such as hacktivists, cybercriminals, pranksters, and researchers.
The Slowloris attack is one of the most simple yet effective DoS attacks that can take down a website with minimal resources and effort. It is also one of the most stealthy and persistent DoS attacks that can evade detection and prevention measures. In the next section, we will explain how the Slowloris attack works in detail and why it is so powerful.
The Basic Mechanism of Slowloris Attacks
To understand how a Slowloris attack works, we need to first understand how a normal HTTP request works. HTTP stands for Hypertext Transfer Protocol, and it is the standard protocol for communication between web browsers and web servers. A typical HTTP request consists of three parts: a request line, a header, and a body.
The request line contains the method (such as GET or POST), the resource (such as /index.html or /login.php), and the version (such as HTTP/1.1) of the request. The header contains additional information about the request, such as the host name, the user agent, the content type, the content length, and more. The body contains the actual data of the request, such as the form data, the file upload, or the cookie. A normal HTTP request looks something like this:
GET /index.html HTTP/1.1
Host: www.example.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:89.0) Gecko/20100101 Firefox/89.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Upgrade-Insecure-Requests: 1
When a web browser sends an HTTP request to a web server, it expects to receive an HTTP response from the server within a certain time limit. The HTTP response also consists of three parts: a status line, a header, and a body.
The status line contains the version (such as HTTP/1.1), the status code (such as 200 OK or 404 Not Found), and the reason phrase (such as OK or Not Found) of the response. The header contains additional information about the response, such as the server name, the content type, the content length, and more. The body contains the actual data of the response, such as the HTML code, the image file, or the cookie. A normal HTTP response looks something like this:
HTTP/1.1 200 OK
Date: Thu, 08 Jun 2023 12:50:58 GMT
Server: Apache/2.4.46 (Ubuntu)
Last-Modified: Mon, 12 Oct 2020 14:28:20 GMT
ETag: "2aa6-5b1f486c7e280"
Accept-Ranges: bytes
Content-Length: 10918
Vary: Accept-Encoding
Content-Type: text/html
<html>
<head>
<title>Example Domain</title>
...
</html>
When a web server receives an HTTP request from a web browser, it processes the request and sends back an HTTP response to the browser. The web server also allocates a certain amount of resources (such as memory, CPU time, and network bandwidth) to handle each request. The web server can only handle a limited number of requests at a time, depending on its configuration and capacity. This limit is called the maximum number of concurrent connections.
A Slowloris attack exploits this limit by sending incomplete or malformed HTTP requests to the web server. A Slowloris attack may look like this:
GET /index.html HTTP/1.1
Host: www.example.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:89.0) Gecko/20100101 Firefox/89.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Upgrade-Insecure-Requests: 1
X-a:
Notice that this request is missing some parts of a normal request:
There is no end-of-line character (\r\n) after the last header field (X-a). There is no blank line (\r\n\r\n) after the header section. There is no body section. This means that this request is incomplete and invalid according to the HTTP protocol. However, some web servers will still accept this request and wait for more data from the client before sending back a response or closing the connection.
A Slowloris attacker will send many such requests to the web server using multiple connections and keep them open as long as possible. The attacker will also periodically send some additional data (such as a space character or another header field) to each connection to prevent the server from timing out and closing the connection. This way, the attacker can occupy all the available connections on the web server and prevent other legitimate users from accessing the website.
The Slowloris attack is very effective because it requires very little resources and bandwidth from the attacker, but consumes a lot of resources and bandwidth from the server. The Slowloris attack is also very stealthy because it does not generate a lot of traffic or error messages that can be detected by firewalls or intrusion detection systems. The Slowloris attack can also bypass some common defenses against DoS attacks, such as rate limiting, IP blocking, or SYN cookies, because it mimics a normal user behavior and does not use a large number of packets or connections.
The Types and Variants of Slowloris Attacks
Since the original Slowloris attack was published in 2009, many types and variants of Slowloris attacks have emerged, targeting different web servers and protocols. Some common types and variants of Slowloris attacks are:
- Slow Headers: This is the basic type of Slowloris attack that we described in the previous section. It sends incomplete or malformed HTTP requests with slow headers to the web server and keeps the connections open. This type of attack can affect any web server that does not validate or limit the header size or the header timeout of HTTP requests.
- Slow Body: This type of Slowloris attack sends complete HTTP requests with slow bodies to the web server and keeps the connections open. It sends the body data very slowly, one byte at a time, to keep the server waiting for more data. This type of attack can affect any web server that does not validate or limit the body size or the body timeout of HTTP requests.
- Slow Read: This type of Slowloris attack sends complete HTTP requests to the web server but reads the HTTP responses very slowly, one byte at a time, to keep the connections open. It forces the server to buffer the response data until it can be sent to the client. This type of attack can affect any web server that does not limit the buffer size or the buffer timeout of HTTP responses.
- Slow POST: This type of Slowloris attack sends POST requests with slow bodies to the web server and keeps the connections open. It sends the body data very slowly, one byte at a time, to keep the server waiting for more data. This type of attack can affect any web server that processes POST requests, such as those that handle form submissions or file uploads.
- Slow SSL: This type of Slowloris attack sends SSL/TLS handshake requests with slow headers or bodies to the web server and keeps the connections open. It sends the handshake data very slowly, one byte at a time, to keep the server waiting for more data. This type of attack can affect any web server that supports SSL/TLS encryption, such as those that use HTTPS protocol.
- Slow HTTPS: This type of Slowloris attack combines Slow SSL and Slow Headers or Slow Body attacks to target HTTPS protocol. It sends SSL/TLS handshake requests with slow headers or bodies and then sends HTTP requests with slow headers or bodies over the encrypted connection. This type of attack can affect any web server that supports HTTPS protocol.
Other variants can use different methods (such as PUT or DELETE) or resources (such as /cgi-bin or /admin) to trigger different behaviors on the web server. Other variants may also use different techniques (such as encryption, proxy support, randomization, or multithreading) to enhance their effectiveness or stealthiness.
Impact of Slowloris Attacks on Web Servers and Applications
Slowloris attacks can have a significant impact on web servers and applications, affecting their performance and functionality. Here you can find some effects of Slowloris attacks:
- Reduced availability: Slowloris attacks can reduce the availability of web servers and applications by consuming all the available connections and preventing other legitimate users from accessing the website. This can result in a denial-of-service (DoS) condition, where the website becomes slow or unreachable for the users. This can also affect the reputation and revenue of the website owner, as well as the satisfaction and loyalty of the users.
- Increased resource consumption: Slowloris attacks can increase the resource consumption of web servers and applications by forcing them to allocate and maintain more resources (such as memory, CPU time, and network bandwidth) for each connection. This can result in a degradation of performance, as well as an increase in operational costs and energy consumption. This can also create a vulnerability for other types of attacks, such as memory exhaustion or buffer overflow attacks, that can exploit the excessive resource usage.
- Impaired functionality: Slowloris attacks can impair the functionality of web servers and applications by interfering with their normal operations and processes. For example, some web servers may have a limit on the number of concurrent requests or processes that they can handle, and exceeding this limit may cause them to crash or malfunction. Some web applications may also have a dependency on the completion or timing of certain requests or processes, and delaying or blocking them may cause them to fail or behave unexpectedly.
Slowloris attacks can cause serious damage to the web server and application, as well as to the website owner and users.
How to Detect and Prevent Slowloris Attacks
Slowloris attacks can be difficult to detect and prevent, as they do not generate a lot of traffic or error messages that can be easily noticed by firewalls or intrusion detection systems. Here you can find tools and methods that can help to detect and prevent Slowloris attacks:
- Monitoring tools: Monitoring tools can help to detect Slowloris attacks by analyzing the traffic and performance of the web server and application. For example, some monitoring tools can measure the number of concurrent connections, the response time, the resource usage, and the error rate of the web server and application. If these metrics show an abnormal increase or decrease, it may indicate a Slowloris attack. Some monitoring tools can also alert the website owner or administrator when a Slowloris attack is detected, and provide some information about the source and nature of the attack.
- Configuration tools: Configuration tools can help to prevent Slowloris attacks by adjusting the settings and parameters of the web server and application. For example, some configuration tools can limit the number of concurrent connections, the header size, the header timeout, the body size, the body timeout, the buffer size, and the buffer timeout of the web server and application. These limits can help to reduce the impact of Slowloris attacks by closing or rejecting incomplete or malformed requests or responses. Some configuration tools can also enable or disable certain features or modules of the web server and application that may be vulnerable or unnecessary for Slowloris attacks.
- Security tools: Security tools can help to prevent Slowloris attacks by filtering or blocking malicious traffic or requests from reaching the web server and application. For example, some security tools can use signatures or heuristics to identify and block Slowloris requests based on their characteristics or patterns. Some security tools can also use whitelists or blacklists to allow or deny access to certain IP addresses or domains that may be involved in Slowloris attacks. Some security tools can also use rate limiting or throttling to control the frequency or intensity of requests from certain sources or destinations that may be involved in Slowloris attacks.
One of the most effective security tools that can protect against Slowloris attacks is PowerWAF. PowerWAF is a web application firewall (WAF) that provides comprehensive protection for web servers and applications against various types of attacks, including Slowloris attacks. PowerWAF can detect and block Slowloris requests using advanced algorithms and rules that can distinguish between legitimate and malicious traffic.
Known Servers Vulnerable to Slowloris Attacks
Slowloris attacks can affect any web server that does not validate or limit the header size, the header timeout, the body size, the body timeout, the buffer size, or the buffer timeout of HTTP requests or responses. Some web servers are more vulnerable than others due to their design or configuration.
The most vulnerable web servers are those that are thread-based, such as Apache HTTP Server 1.x and 2.x, dhttpd 0.9c and Internet Information Services (IIS) 6.0 and earlier. Thread-based web servers use a separate thread for each connection, and each thread consumes a certain amount of resources (such as memory and CPU time). When a Slowloris attack occupies all the available threads on the web server, it prevents the web server from processing other requests.
Some web servers that support SSL/TLS encryption or HTTPS protocol are also vulnerable to Slowloris attacks, such as Apache HTTP Server 2.2.15 and earlier and Internet Information Services (IIS) 7.0 and earlier. SSL/TLS encryption or HTTPS protocol adds an extra layer of security and complexity to the communication between the web server and the client. However, it also adds an extra layer of vulnerability and overhead to the web server. A Slowloris attack can exploit this by sending slow SSL/TLS handshake requests or slow HTTP requests over the encrypted connection.
NGINX 1.5.9 and earlier are vulnerable too to Slowloris attacks using their default configuration.
In any case, it is important to test and monitor your web server for any signs of Slowloris attacks and apply appropriate mitigation measures.
Recommendations for Web Server Configuration to Mitigate Slowloris Attacks
Web servers are often the target of Slowloris attacks, which can consume all the available connections on the web server and cause a denial-of-service (DoS) condition. To prevent or mitigate such attacks, web server administrators should configure their web servers properly and use appropriate security tools and modules.
The next are the recommendations for web server configuration to mitigate Slowloris attacks:
- Set a timeout for HTTP requests: One of the ways to prevent Slowloris attacks is to set a timeout for receiving the request line, the request header, and the request body of an HTTP request. If the client does not send the complete request within the specified time, the web server should close the connection. This can help to prevent Slowloris attacks that send incomplete or malformed requests or send data very slowly.
- Limit the number of concurrent connections per IP address: Another way to prevent Slowloris attacks is to limit the number of concurrent connections that a single IP address can open on the web server. This can help to prevent Slowloris attacks that use multiple connections from the same source.
Configuring Apache Prevent Slowloris Attacks
Slowloris attacks can exploit the way Apache handles HTTP requests and consume all the available connections on the web server, causing a denial-of-service (DoS) condition.
Fortunately, there are some ways to configure Apache HTTP Server to prevent or mitigate Slowloris attacks:
- Use the mod_reqtimeout module: This module allows you to set a timeout for receiving the request line and the request header of an HTTP request. If the client does not send the complete request within the specified time, the connection is closed. This can help to prevent Slowloris attacks that send incomplete or malformed requests. To use this module, you need to enable it and add something like this to your configuration file:
<IfModule reqtimeout_module>
RequestReadTimeout header=10-20,MinRate=500 body=10,MinRate=500
</IfModule>
This example sets a timeout of 10 seconds for receiving the request line, a timeout of 10-20 seconds for receiving the request header (depending on the size of the header), and a timeout of 10 seconds for receiving the request body. It also sets a minimum data rate of 500 bytes per second for both the header and the body. You can adjust these values according to your needs.
- Use the mod_limitipconn module: This module allows you to limit the number of simultaneous connections from a single IP address. This can help to prevent Slowloris attacks that use multiple connections from the same source. To use this module, you need to enable it and add something like this to your configuration file:
<IfModule mod_limitipconn.c>
<Location />
MaxConnPerIP 30
</Location>
</IfModule>
This example limits the number of connections per IP address to 30 for any location on the web server. You can adjust this value according to your needs.
- Use other modules: There are other modules that can help to prevent Slowloris attacks by adding various checks or limits to HTTP requests or responses, such as mod_qos, mod_evasive, mod_security, mod_noloris, and mod_antiloris. You can find more information about these modules and how to use them on their respective websites or documentation.
Conclusion: How to Protect Your Website from Slowloris Attacks
In this article, we have explained what a Slowloris attack is and how it works, what impact it can have on your web server and application, how to detect and prevent it, and what best practices you can follow to mitigate it.
Now you should have a better understanding of this silent killer of websites and how to protect yourself from it. However, remember that Slowloris attacks are not the only type of DoS attacks that can threaten your website security and performance. There are many other types of DoS attacks that can exploit different vulnerabilities or features of your web server or application. Therefore, it is important to always keep your web server and application updated and patched, monitor your traffic and performance regularly, and use a reliable security tool such as PowerWAF to defend against various types of attacks.
We hope you found this article useful and informative. If you have any questions or feedback, please feel free to contact us or leave a comment below. Thank you for reading and stay safe!
Start your 7 days Free Trial
Implement WAF & CDN for your websites