
One of the most common computer attacks on websites, and the one with the highest fines, is the theft and subsequent filtering of databases.
These types of events damage the company’s prestige in front of the community.
How does the break-in take place?
According to our experience, database theft occurs mainly in three ways:
1. Using SQL injection
Although it is hard to believe, SQL injection is not only used to break the Login forms, but with the correct use we can obtain the complete databases associated with a website.
For this purpose there is specific software, with which, once found an injection point, it is possible to obtain the complete database and save it locally.
What is an injection point? It is a URL vulnerable to SQL injections. It can be a login form, a password reminder form, or any part of our website with dynamically generated content.
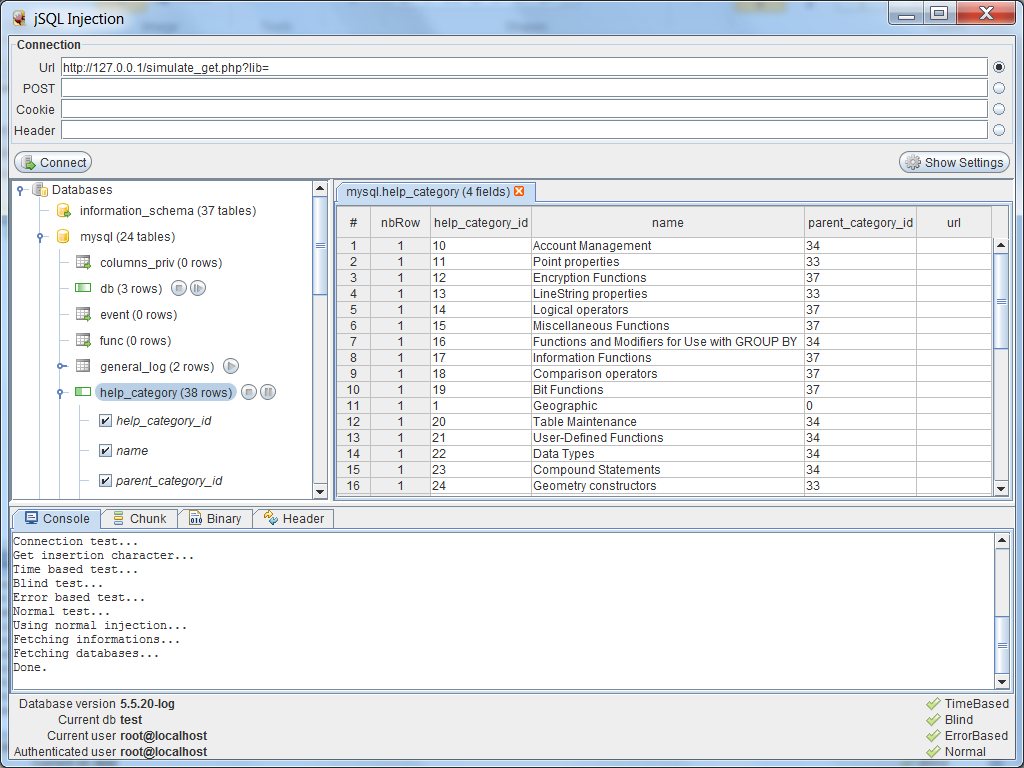
With JSQL it is possible to obtain complete databases
from a SQL injection point
2. With malware
This procedure requires that the attacker succeeds in uploading malware to the server in order to take control of it. In general, the process for doing this can be too simple.
Once the malware is installed, the attacker has full access to the file system and databases on the server.
He can generate a backup of the database and then download it using the web server.
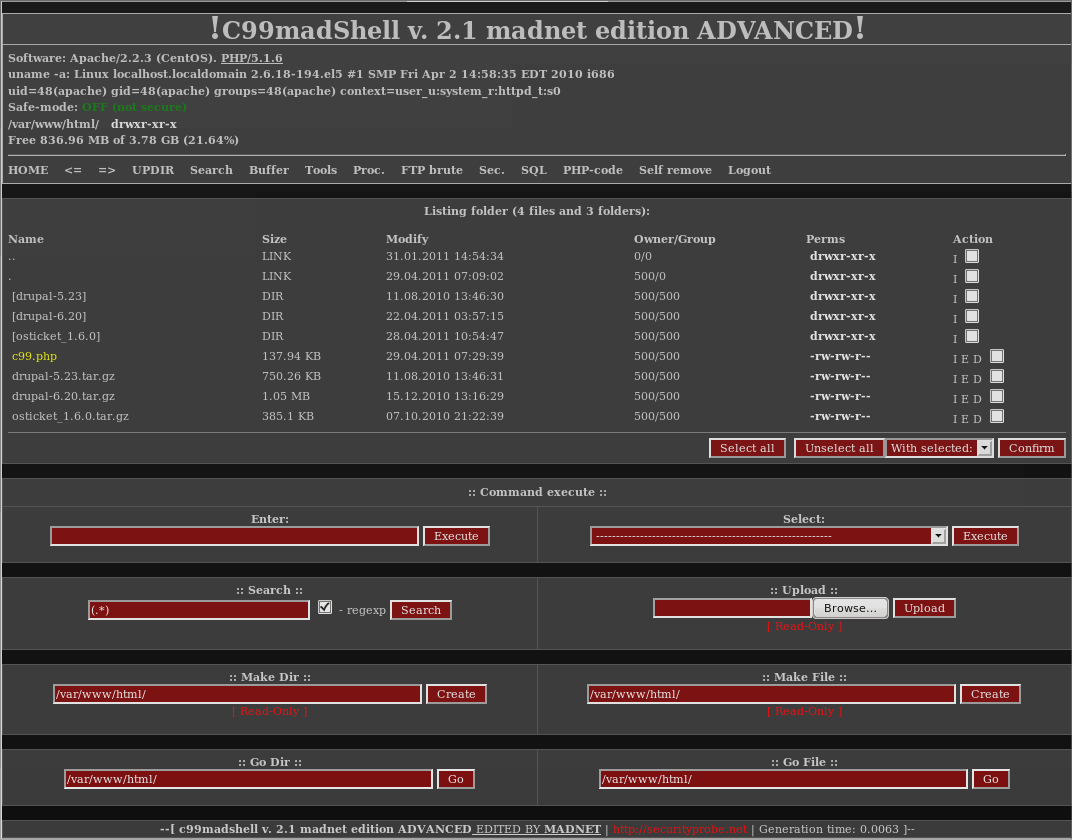
c99shell: Malware used to take silent control
of a web server and its databases
3. With brute force or a vulnerability scanner
Many vulnerability scanners search websites for the presence of database backups. When one is found, the attacker simply downloads it and obtains the complete databases. How can we protect our websites?
Unfortunately, protection with simple methods is not always efficient. The code on our websites or the libraries you use may have vulnerabilities that can be exploited sooner or later.
For this reason, at Pyxsoft PowerWAF we have worked to incorporate defense in this and other areas for websites.
With PowerWAF, we prevent SQL injection at any point, with the use of a tokenizer and regular expressions.
PowerWAF prevents malware from being uploaded to servers. And if malware is already installed, PowerWAF prevents it from being used.
In addition, PowerWAF monitors the traffic generated by the web server and if it detects that a database file is being downloaded, it automatically drops the connection preventing its download.