DDoS Attacks
What are DoS and DDoS Attacks?

DoS stands for Denial of Service Attack and DDoS stands for Distributed Denial of Service Attack.
A denial of service attack is a type of attack that aims to prevent a system, such as a website, server or network, from continuing to deliver its service in a normal manner, preventing its normal use by legitimate users.
There are different ways of producing denial of service. We will review these forms according to the layer of the OSI model where they are concentrated.
Understanding the OSI Model
The OSI (Open Systems Interconnection) model is a conceptual framework used to understand the different layers of network communication. It consists of seven layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application. By examining DDoS attacks through the lens of the OSI model, we can identify the specific layers targeted by different attack types.
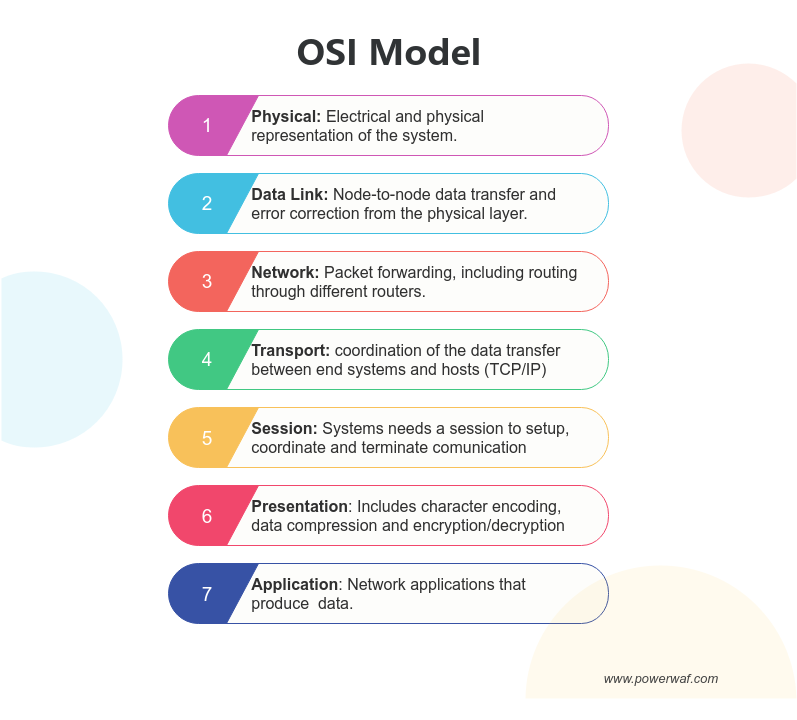
Although denial-of-service attacks can occur at any of these layers, the most common are:
Level 4 DDoS Attacks
Level 4 DDoS attacks, also known as Transport Layer Attacks, focus on exploiting vulnerabilities at the Transport layer of the OSI model. These attacks primarily target protocols such as TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). By overwhelming the target system with a massive volume of connection requests, Level 4 attacks exhaust the system's resources, leading to service disruptions or complete unavailability.
Level 7 DDoS Attacks
Level 7 DDoS attacks, also referred to as Application Layer Attacks, occur at the highest layer of the OSI model: the Application layer. These attacks specifically target the web applications and services running on the target system. Level 7 attacks aim to exploit vulnerabilities in the way applications process and respond to user requests. By overwhelming the application layer with malicious requests, these attacks can lead to application crashes, data leaks, or unauthorized access.
Types of DDoS Attacks
Layer 4 DDoS Attacks
SYN Flood Attacks
SYN flood attacks target the TCP three-way handshake process. The attacker floods the target system with a large number of SYN packets, overwhelming the system's resources. As the target tries to establish a connection by sending SYN-ACK packets in response, the attacker does not respond with the final ACK packet, resulting in the target's resources being tied up in waiting for the completion of the connection.
UDP Flood Attacks
UDP flood attacks exploit vulnerabilities in the User Datagram Protocol (UDP). The attacker sends a high volume of UDP packets to the target system, overwhelming its UDP ports. Since UDP is connectionless and does not require a handshake, it is easier to initiate a flood attack, exhausting the system's resources and causing service disruption.
Layer 7 DDoS Attacks
HTTP Flood Attacks
HTTP flood attacks target the application layer of the OSI model by overwhelming the target's web server with a massive volume of HTTP requests. The attacker aims to exhaust the target's web server resources, causing it to become unresponsive or unavailable. These attacks can be launched using botnets or by exploiting vulnerable HTTP proxies.
Slowloris Attacks
Slowloris attacks exploit the way web servers handle simultaneous connections. The attacker initiates multiple connections to the target server but sends the HTTP request slowly, keeping the connections open for as long as possible. By consuming the server's available connection slots, Slowloris attacks can prevent legitimate users from accessing the server, causing denial of service.
DNS Amplification Attacks
DNS amplification attacks leverage vulnerable DNS servers to amplify the volume of traffic directed at the target system. The attacker sends small DNS queries with spoofed source IP addresses to open DNS resolvers, which respond with significantly larger DNS responses. This amplification technique allows the attacker to generate a high volume of traffic directed towards the target, overwhelming its resources.
SSL/TLS Attacks
SSL/TLS attacks target the encryption layer used to secure web communications. Attackers can launch SSL/TLS-based DDoS attacks by initiating numerous SSL/TLS handshakes, exhausting server resources and causing service degradation. These attacks exploit the computational cost associated with establishing secure connections.
Conclusion
Layer 4 DDoS attacks, such as SYN flood attacks and UDP flood attacks, primarily target the network and transport layers of the OSI model. On the other hand, Layer 7 DDoS attacks, including HTTP flood attacks, Slowloris attacks, DNS amplification attacks, and SSL/TLS attacks, focus on overwhelming the application layer of the OSI model. By understanding the different attack types and their targeted layers, organizations can implement appropriate defense strategies to protect their networks and mitigate the impact of DDoS attacks.
Understanding the Impact of DDoS Attacks
Distributed Denial of Service (DDoS) attacks can have severe consequences for individuals, businesses, and even entire networks. By overwhelming a target system's resources and making it inaccessible to legitimate users, DDoS attacks can disrupt operations, cause financial losses, damage reputation, and pose significant security risks. It is crucial to comprehend the impact of DDoS attacks to develop effective mitigation strategies
Recognizing the Signs of a DDoS Attack
Detecting a Distributed Denial of Service (DDoS) attack in its early stages is crucial for effective mitigation and minimizing the impact on targeted systems. By recognizing the signs of a DDoS attack, organizations can take immediate action to protect their networks and services. Here are key indicators to watch for:
1. Unusually High Network Traffic
A sudden surge in network traffic, especially if it exceeds the normal patterns or expected thresholds, can be a strong indication of a DDoS attack. Monitor network traffic levels regularly and look for significant spikes or sustained abnormally high levels that are unrelated to typical user activity.
2. Service Performance Degradation
If your network or web services experience a sudden slowdown, unresponsiveness, or intermittent outages, it could be a sign of a DDoS attack. Pay attention to user complaints, increased latency, or unexplained drops in service quality, as these could indicate the presence of an ongoing attack.
3. Inability to Access Specific Resources
If certain web pages, applications, or online services become inaccessible, while other parts of your network remain functional, it might indicate a targeted DDoS attack. Attackers often focus on specific resources or services to disrupt specific operations or cause maximum impact on targeted systems.
4. Increased Network Errors
A sudden increase in network errors, such as timeouts, failed connections, or error messages, can point to a potential DDoS attack. These errors may occur when the target system's resources are overwhelmed, resulting in the inability to handle incoming requests effectively.
5. Unusual Patterns in Traffic Sources
Monitoring the source IP addresses of incoming traffic can help identify a DDoS attack. Look for a significant number of requests coming from a limited set of IP addresses or from geographically dispersed sources simultaneously. This pattern may indicate that a botnet is being used to launch the attack.
6. Unusual Traffic Patterns
Analyze your network traffic patterns regularly to detect any abnormal behavior. Look for patterns such as a high number of connections from a single IP address, an unusual distribution of packet sizes, or traffic that doesn't adhere to typical user behavior. These anomalies can indicate the presence of a DDoS attack.
The Motives Behind DDoS Attacks
Distributed Denial of Service (DDoS) attacks are orchestrated by malicious actors with specific motives and objectives. Understanding the motives behind these attacks can help organizations better prepare for and mitigate potential risks. Some common motives behind DDoS attacks:
Revenge and Vendetta
In some cases, DDoS attacks are launched as a form of revenge or retaliation against an individual, organization, or entity. Attackers may seek retribution for perceived wrongdoings, personal conflicts, or ideological differences. These attacks are often intended to disrupt the target's operations and cause inconvenience or financial harm.
Competitive Advantage
DDoS attacks can be driven by a desire to gain a competitive advantage in the business landscape. Competitors or adversaries may launch DDoS attacks against a rival organization to disrupt its services, tarnish its reputation, or gain an edge in the market. By rendering a competitor's website or services inaccessible, attackers aim to divert customers and clients to their own offerings.
Ideological or Political Motivations
Some DDoS attacks are politically or ideologically motivated. Hacktivist groups or individuals may target organizations or government entities to express dissent, promote a specific agenda, or protest against perceived injustices. These attacks are often aimed at high-profile targets to attract media attention and raise awareness about certain social or political issues.
Financial Gain
DDoS attacks can also be financially motivated. Attackers may launch DDoS attacks against online businesses or financial institutions with the intention of disrupting their operations and extorting money in exchange for stopping the attack. Additionally, attackers may target organizations to create distractions while carrying out other cybercriminal activities, such as data breaches or fraud.
Cyber Warfare and State-Sponsored Attacks
Nation-states and state-sponsored actors may employ DDoS attacks as part of cyber warfare strategies. These attacks aim to disrupt critical infrastructure, government systems, or military networks of rival nations. State-sponsored DDoS attacks can cause significant economic damage, political destabilization, or compromise national security.
Testing or Diversion
In some instances, DDoS attacks may be conducted as a testing mechanism or diversion tactic. Attackers may launch small-scale DDoS attacks to assess the target's defenses, identify vulnerabilities, or distract security teams while carrying out more sophisticated cyberattacks, such as data theft or network infiltration.
DDoS (Distributed Denial of Service) is illegal in many countries, including the United States and the European Union. Even if the attack originates from another country, the victim can still press charges and the attacker can still be prosecuted under local or international law. DDoS attacks can cause significant harm to individuals and businesses.
Steps to Protect Your Network from DDoS Attacks
Safeguarding your network against Distributed Denial of Service (DDoS) attacks is crucial to maintain the availability and integrity of your online services. Implementing effective mitigation measures can help minimize the impact of such attacks. Here are some steps to protect your network from DDoS attacks:
Perform Regular Risk Assessments
Conduct a comprehensive risk assessment to identify vulnerabilities in your network infrastructure. Assess the potential impact of a DDoS attack on your organization and evaluate the effectiveness of your current security measures. This assessment will help you prioritize your efforts and allocate resources effectively.
Implement Network Traffic Monitoring
Deploy robust network monitoring tools to continuously monitor your network traffic. This allows you to detect any unusual patterns, spikes in traffic, or anomalies that may indicate a DDoS attack. Monitoring tools can provide valuable insights into your network's health and help you identify potential attacks at an early stage.
PowerWAF offers to infrastructure customers a ready-to-use realtime web based monitoring system
Utilize Traffic Filtering and Rate Limiting
Implement traffic filtering mechanisms to filter out malicious traffic and reduce the impact of DDoS attacks. Configure rate-limiting measures to restrict the number of requests from individual IP addresses or limit traffic based on predefined thresholds. These measures can help mitigate the impact of volumetric attacks and prevent resource exhaustion.
Employ Load Balancers and Redundancy
Distribute incoming traffic across multiple servers using load balancers. Load balancing helps distribute the workload, making it more difficult for attackers to overwhelm a single server. Additionally, establish redundancy by replicating critical resources and services across multiple servers or data centers. This ensures that if one server or data center is affected by a DDoS attack, your services can still remain available.
Deploy a Web Application Firewall (WAF)
Consider utilizing a Web Application Firewall (WAF) like PowerWAF to protect your network from DDoS attacks. A WAF acts as a barrier between your web applications and potential attackers, filtering out malicious traffic and blocking suspicious requests. PowerWAF, with its advanced security features and intelligent threat detection capabilities, can effectively mitigate DDoS attacks and provide an additional layer of protection for your web applications. See how PowerWAF WAF can protect your organization's sites.
Implement DDoS Mitigation Services
Engage with a reliable DDoS mitigation service provider to benefit from their expertise and specialized tools. These services employ advanced techniques, such as traffic scrubbing and traffic diversion, to identify and mitigate DDoS attacks in real-time. DDoS mitigation services can help ensure that your network remains resilient and your services are accessible during an attack.
Develop an Incident Response Plan
Create a comprehensive incident response plan that outlines the steps to be taken in the event of a DDoS attack. Establish clear roles and responsibilities for your incident response team, define communication channels, and practice response procedures through regular drills and simulations. A well-prepared incident response plan enables a swift and coordinated response to minimize the impact of an attack.
PowerWAF has been successfully used by National Cybersecurity Agencies to protect against DDoS attacks against government sites. Learn more about PowerWAF DDOS Protection