Web applications are essential for many businesses and organizations, as they provide various functions and services to their customers and users. However, web applications are also vulnerable to various types of cyberattacks, such as SQL injection, cross-site scripting, denial-of-service, and more. These attacks can compromise the security, performance, and availability of web applications, as well as the data and privacy of their users. To protect web applications from these threats, you need a web application firewall (WAF) like PowerWAF. But what is a WAF, and how does it work?
In this article, we will explain everything you need to know about WAFs, including their types, benefits, challenges, and deployment options.
What is a web application firewall (WAF)?
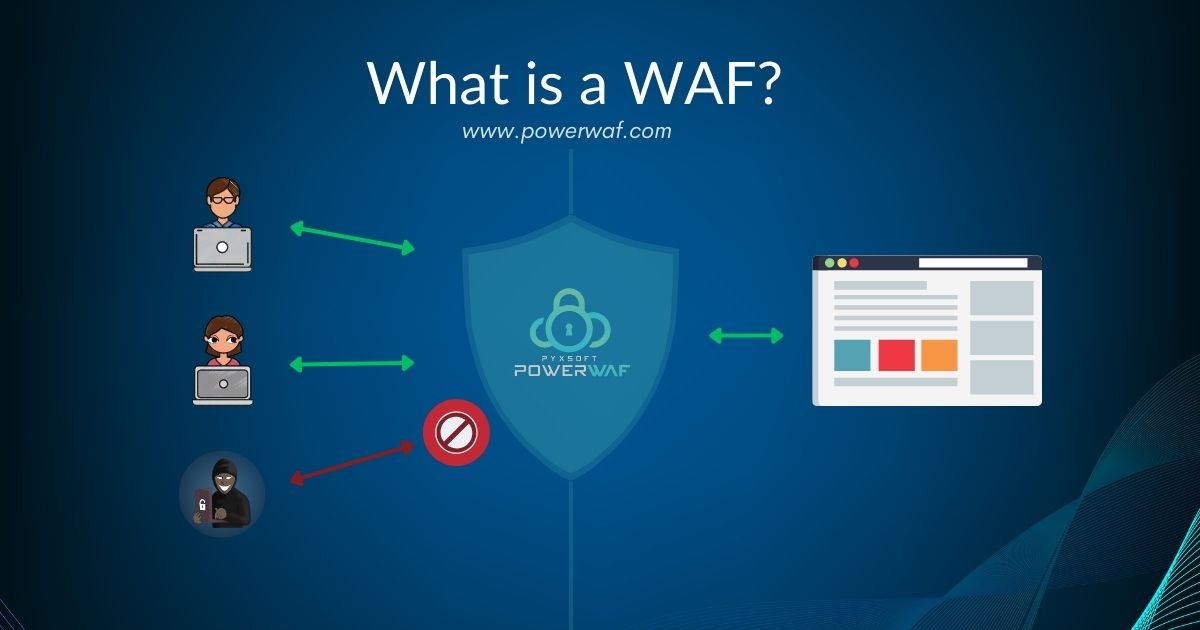
A Web Application Firewall (WAF) is a type of firewall that protects web applications and APIs by filtering, monitoring and blocking malicious web traffic and application-layer attacks. A WAF operates at the protocol layer 7 (in the OSI model), which means it focuses on the content and behavior of the HTTP/HTTPS requests and responses between the web application and the internet. A WAF can help prevent attacks such as cross-site scripting (XSS), SQL injection, cookie manipulation, file inclusion, denial-of-service, and more.
A WAF works by applying a set of rules or policies to the web traffic, which are designed to identify and block any malicious or suspicious activity. The policies can be based on various criteria, such as the source IP address, the request method, the request headers, the request body, the response status code, the response headers, the response body, and more. The policies can also be customized to suit the specific needs and characteristics of each web application.
A WAF can be deployed in different ways, depending on the architecture and environment of the web application:
- Network-based WAF: This is a hardware-based solution that is installed locally on the network infrastructure. It offers low latency and high performance, but it is also expensive and requires physical maintenance.
- Host-based WAF: This is a software-based solution that is integrated into the web application or server. It offers more flexibility and customization, but it also consumes local resources and adds complexity to the implementation.
- Cloud-based WAF: This is a service-based solution that is hosted on a cloud platform. It offers scalability and ease of use, but it also depends on the availability and security of the cloud provider. PowerWAF is a cloud solution with 99.9% of availability, offering dynamic routes in case of hardware or network failures
A WAF is an essential security component for any web application that needs to accept and respond to requests from the internet. By using a WAF, you can protect your web application from common vulnerabilities and threats, as well as comply with industry standards and regulations. However, a WAF is not a silver bullet that can guarantee complete security for your web application. You still need to follow best practices for developing, testing, and maintaining secure web applications.
Why do you need a WAF?
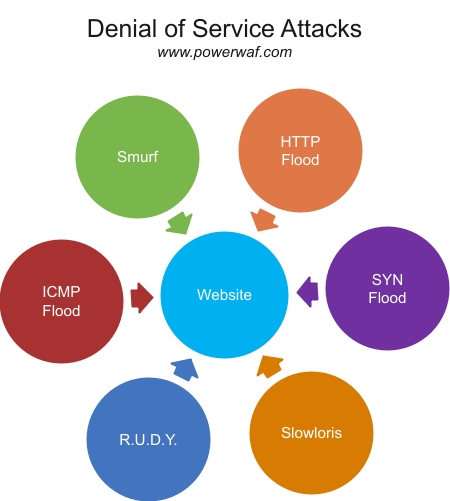
You need a WAF because web applications are constantly exposed to various cyberattacks that can compromise their security, performance, and availability. Web applications are often the target of hackers who want to steal, manipulate, or destroy data, disrupt services, or gain unauthorized access to systems or networks. Some attacks are:
- Cross-site scripting (XSS): This is an attack that injects malicious scripts into web pages that are viewed by other users. The scripts can execute in the browser of the victim and perform actions such as stealing cookies, redirecting to malicious sites, or displaying fake content.
- SQL injection: This is an attack that exploits a vulnerability in the web application’s database query. The attacker can insert malicious SQL statements into the input fields of the web application and execute them on the database server. The results can include data theft, data corruption, or database damage.
- Cookie manipulation: This is an attack that alters or forges the cookies that are used to store user information and preferences on the web application. The attacker can use the modified cookies to impersonate other users, bypass authentication, or access restricted areas.
- File inclusion: This is an attack that exploits a vulnerability in the web application’s file handling. The attacker can include malicious files from remote or local sources into the web application and execute them on the server. The results can include code execution, data theft, or server compromise.
- Denial-of-service (DoS): This is an attack that overwhelms the web application’s resources and prevents it from functioning properly. The attacker can send a large number of requests or packets to the web application or its network, causing it to slow down, crash, or become unavailable.
These attacks can have serious consequences for your web application and your business:
- Loss of data and privacy: Your web application may store sensitive information such as personal details, financial records, or confidential documents. If these data are stolen or leaked by hackers, you may face legal issues, reputational damage, or customer dissatisfaction.
- Loss of revenue and productivity: Your web application may provide essential functions or services to your customers or users. If these functions or services are disrupted or unavailable due to cyberattacks, you may lose sales opportunities, customer loyalty, or user satisfaction.
- Loss of compliance and trust: Your web application may need to comply with industry standards and regulations such as PCI DSS, GDPR, HIPAA, or ISO 27001. If your web application is breached or compromised by hackers, you may face fines, penalties, or lawsuits. You may also lose the trust and confidence of your customers, users, partners, or stakeholders.
A WAF can help you prevent these attacks and consequences by providing a layer of protection between your web application and the internet. A WAF can filter and monitor the web traffic and block any malicious or suspicious requests before they reach your web application.
What are the benefits of using a WAF?
Using a WAF has several benefits for your web application:
- Improving security. A WAF helps improve the security of your web applications by protecting against hundreds of possible attack vectors, from denial-of-service attacks to application-specific attacks to database theft.
- Improving performance and scalability. A WAF can reduce the load on your web application by caching static content, compressing data, or balancing traffic. A WAF can also scale up or down according to the demand and traffic volume of your web application.
- Improving visibility and reporting. A WAF can provide you with detailed logs and analytics of the web traffic and activity on your web application. You can use this information to identify trends, patterns, anomalies, or threats on your web application and take appropriate actions.
- Improving customization and flexibility. A WAF can allow you to customize and configure its policies and rules according to your specific needs and preferences. You can also choose from different types and deployment options of WAFs depending on your architecture and environment.
- Preventing SQL injection. SQL injection is an attack that exploits a vulnerability in the web application’s database query. The attacker can insert malicious SQL statements into the input fields of the web application and execute them on the database server. This can result in data theft, data corruption, or database damage. A WAF can prevent SQL injection by filtering and sanitizing the user input and blocking any malicious SQL queries.
- Obstructing cross-site scripting (XSS). XSS is an attack that injects malicious scripts into web pages that are viewed by other users. The scripts can execute in the browser of the victim and perform actions such as stealing cookies, redirecting to malicious sites, or displaying fake content. A WAF can obstruct XSS by detecting and removing any malicious scripts from the web pages and blocking any suspicious requests.
- Mitigating denial-of-service (DoS) attacks. DoS attacks are attacks that overwhelm the web application’s resources and prevent it from functioning properly. The attacker can send a large number of requests or packets to the web application or its network, causing it to slow down, crash, or become unavailable. A WAF can mitigate DoS attacks by limiting the rate of requests, caching static content, balancing traffic, or blocking any abnormal or malicious requests.
- Stopping cookie poisoning. Cookie poisoning is an attack that modifies or forges the cookies that store user information and preferences on the web application. This can allow the attacker to impersonate other users, bypass authentication, or access restricted areas. A WAF can prevent cookie poisoning by validating and encrypting the cookies and blocking any tampered or invalid cookies.
What are the main components of a WAF?
A WAF consists of several components that work together to provide protection for web applications and APIs:
- Web application firewall policy. A WAF policy is the overall configuration of the WAF service, including origin management, protection rule settings, and bot detection features. A WAF policy defines how the WAF filters and monitors the web traffic and blocks or allows requests based on various criteria. A WAF policy can be customized to suit the specific needs and characteristics of each web application or API.
- Protection rules. Protection rules are the core of the WAF’s logic and functionality. They are the rules that determine what kind of requests are considered malicious or suspicious and how they should be handled by the WAF. Protection rules can be based on various factors, such as the source IP address, the request method, the request headers, the request body, the response status code, the response headers, the response body, and more. Protection rules can also be aligned with industry standards and regulations, such as the OWASP Top 10 list of common web application vulnerabilities.
- Web application firewall engine. The WAF engine is the component that executes the protection rules and applies them to the web traffic. The WAF engine analyzes each request and response and compares them with the protection rules. If a request or response matches a protection rule, the WAF engine takes the appropriate action, such as blocking, allowing, logging, or alerting. The WAF engine can also perform other functions, such as caching static content, compressing data, or balancing traffic.
- Web application firewall logs and analytics. The WAF logs and analytics are the component that records and reports the web traffic and activity on the web application or API. The WAF logs and analytics provide detailed information about each request and response, such as the source IP address, the request method, the request headers, the request body, the response status code, the response headers, the response body, and more. The WAF logs and analytics also provide insights into trends, patterns, anomalies, or threats on the web application or API and help with troubleshooting and optimization.
How does a WAF filter and monitor HTTP/HTTPS traffic?
A WAF filters and monitors HTTP/HTTPS traffic by applying a set of rules or policies to the web traffic, which are designed to identify and block any malicious or suspicious activity. The policies can be based on various criteria, such as the source IP address, the request method, the request headers, the request body, the response status code, the response headers, the response body, and more. The policies can also be aligned with industry standards and regulations, such as the OWASP Top 10 list of common web application vulnerabilities.
A WAF checks each request and response and compares them with the policies. If a request or response matches a policy, the WAF takes the appropriate action, such as blocking, allowing, logging, or alerting. The WAF can also perform other functions, such as caching static content, compressing data, or balancing traffic.
A WAF can filter and monitor HTTP/HTTPS traffic in different ways, depending on the type of WAF:
- Blacklist WAF: This is a type of WAF that operates based on a blocklist (negative security model) that protects against known attacks. It rejects any requests or responses that match the blocklist criteria.
- Allow-list WAF: This is a type of WAF that operates based on an allowlist (positive security model) that only admits traffic that has been pre-approved. It rejects any requests or responses that do not match the allowlist criteria.
- Signature-based WAF: This is a type of WAF that operates based on a signature (pattern) that matches known attacks. It blocks any requests or responses that match the signature criteria.
- Behavior-based WAF: This is a type of WAF that operates based on the behavior (anomaly) that deviates from normal or expected traffic. It blocks any requests or responses that exceed a certain threshold or score.
- Hybrid WAF: This is a type of WAF that combines both signature-based and behavior-based filtering methods. It blocks any requests or responses that match the signature criteria or exceed the behavior threshold or score.
How can a WAF protect against Denial of Service (DoS) attacks?

A WAF can protect against DoS attacks by limiting the rate of requests, caching static content, balancing traffic, or blocking any abnormal or malicious requests.
A WAF can limit the rate of requests by setting a threshold for the number of requests that can be accepted from a single source or destination within a given time period. If the threshold is exceeded, the WAF can block or delay the excess requests and prevent them from reaching the web application.
A WAF can cache static content by storing copies of frequently requested or unchanging web pages or files on the WAF server. This can reduce the load on the web application server and improve the response time for the users.
A WAF can also compress data by reducing the size of the web pages or files before sending them to the users. This can save bandwidth and improve the performance of the web application.
A WAF can balance traffic by distributing the incoming requests among multiple web application servers or instances. This can increase the availability and scalability of the web application and prevent any single server from being overloaded. A WAF can also monitor the health and status of each server and redirect the traffic to the best available server.
A WAF can block any abnormal or malicious requests by applying a set of rules or policies to the web traffic, which are designed to identify and block any malicious or suspicious activity. The rules or policies can be based on various criteria. The rules or policies can also be aligned with industry standards and regulations, such as the OWASP Top 10 list of common web application vulnerabilities. A WAF can also use machine learning or artificial intelligence to detect and block any anomalous or unknown attacks.
What are the advantages and disadvantages of each type of WAF?
Each type of WAF has its own advantages and disadvantages:
| Type | Advantages | Disadvantages |
|---|---|---|
| Network-based WAF | - Low latency and high performance | - Large upfront investment |
| - Can handle high traffic volume | - Ongoing maintenance costs | |
| - Can protect multiple web applications | - High IT operational costs/headcount | |
| - Updates and maintenance managed by the end user | ||
| Host-based WAF | - More flexibility and customization | - Consumes local server resources |
| - Can be tailored to specific web applications | - Adds complexity to the implementation | |
| - Can protect against internal threats | - Requires software installation and configuration | |
| - May have compatibility issues with other software | ||
| Cloud-based WAF | - Scalability and ease of use | - Depends on the availability and security of the cloud provider |
| - Affordable and cost-effective | - May have limited customization options | |
| - Regularly updated and maintained by the service provider | - May have latency or performance issues | |
| - Can protect against distributed attacks |
Why choose PowerWAF & CDN?
PowerWAF & CDN is a cloud-based solution that provides advanced protection and performance for web applications and APIs. PowerWAF & CDN combines the features and benefits of PowerWAF, a web application firewall service that uses machine learning and artificial intelligence to detect and block unknown attacks in real time, and CDN, a content delivery network that uses anycast DNS servers to speed up web content delivery and performance.
By choosing PowerWAF & CDN, you can enjoy the following advantages:
- Security: You can protect your web applications and APIs from a wide range of attacks, such as SQL injection, cross-site scripting, DDoS, botnets, and more. You can also customize your WAF rules and policies according to your specific needs and preferences. You can also leverage PowerWAF’s global threat intelligence network that shares insights and updates from other users.
- Performance: You can reduce latency, bandwidth, and load time for your web applications and APIs by using PowerWAF’s CDN and anycast DNS servers. A CDN or content delivery network is a network of servers that store and deliver your web content to users based on their geographic location. An anycast DNS server is a server that routes DNS queries to the nearest or best available server.
- Scalability: You can adjust your WAF settings and rules according to your web application needs and preferences. You can also choose from different pricing plans that suit your budget and traffic volume. You can also rely on PowerWAF’s high availability and performance.
- Ease of use: You can deploy PowerWAF & CDN in minutes without any hardware or software installation. You can also manage and monitor your web application security and performance from a user-friendly web interface.
- Load balancing: You can distribute your web application traffic across multiple servers or regions using PowerWAF’s load balancing feature. This can help you balance the workload, improve the responsiveness, and avoid overloading or crashing of any single server.
- High concurrency: You can handle many requests simultaneously in parallel using PowerWAF global CDN. This can help you cope with peak traffic, improve the throughput, and reduce the waiting time for your users.
Start your 7 days Free Trial
Implement WAF & CDN for your websites